- 24. März 2017
- Veröffentlicht durch: Admin
- Kategorie: Allgemein


A recent, massive spike in sophisticated and successful phishing attacks is prompting many universities to speed up timetables for deploying mandatory two-factor authentication (2FA) — requiring a one-time code in addition to a password — for access to student and faculty services online. This is the story of one university that accelerated plans to require 2FA after witnessing nearly twice as many phishing victims in the first two-and-half months of this year than it saw in all of 2015.
 Bowling Green State University in Ohio has more than 20,000 students and faculty, and like virtually any other mid-sized state school its Internet users are constantly under attack from scammers trying to phish login credentials for email and online services.
Bowling Green State University in Ohio has more than 20,000 students and faculty, and like virtually any other mid-sized state school its Internet users are constantly under attack from scammers trying to phish login credentials for email and online services.
BGSU had planned later this summer to make 2FA mandatory for access to the school’s portal — the primary place where students register for classes, pay bills, and otherwise manage their financial relationship to the university.
That is, until a surge in successful phishing attacks resulted in several students having bank accounts and W-2 tax forms siphoned.
On March 1, 2017 all BGSU account holders were required to change their passwords, and on March 15, 2017 two-factor authentication (Duo) protection was placed in front of the MyBGSU portal [full disclosure: Duo is a longtime advertiser on KrebsOnSecurity].
Matt Haschak, director of IT security and infrastructure at BGSU, said the number of compromised accounts detected at BGSU has risen from 250 in calendar year 2015 to 1000 in 2016, and to approximately 400 in the first 75 days of 2017.
Left unchecked, phishers are on track to steal credentials from nearly 10 percent of the BGSU student body by the end of this year. The university has offered 2FA options for its portal access since June 2016, but until this month few students or faculty were using it, Haschak said.
“We saw very low adoption when it was voluntary,” he said. “And typically the people who adopted it were not my big security risks.”
Haschak said it’s clear that the scale and size of the phishing problem is hardly unique to BGSU.
“As I keep preaching to our campus community, this is not unique to BGSU,” Haschak said. “I’ve been talking a lot lately to my counterparts at universities in Ohio and elsewhere, and we’re all getting hit with these attacks very heavily right now. Some of the phishing scams are pretty good, but unfortunately some are god-awful, and I think people are just not thinking or they’re too busy in their day, they receive something on their phone and they just click it.”
Last month, an especially tricky phishing scam fooled several students who are also employed at the university into giving away their BGSU portal passwords, after which the thieves changed the victims’ direct deposit information so that their money went to accounts controlled by the phishers.
In other scams, the phishers would change the routing number for a bank account tied to a portal user, and then cancel that student’s classes near the beginning of a semester — thus kicking off a fraudulent refund.
One of the victims even had a fraudulent tax refund request filed in her name with the IRS as a result, Haschak said.
“They went in and looked at her W-2 information, which is also available via the portal,” he said.
While BGSU sends an email each time account information is changed, the thieves also have been phishing faculty and staff email accounts — which allows the crooks to delete the notification emails.
“The bad guys also went in and deleted the emails we sent, and then deleted the messages from the victim’s trash folder,” Haschak said.
Part of BGSU’s messaging to students and faculty about the new 2FA requirements for university portal access.
Ultimately, BGSU opted to roll out 2FA in a second stage for university email, mainly because of the logistics and support issues involved, but also because they wanted to focus on protecting the personally identifiable information in the BGSU portal as quickly as possible.
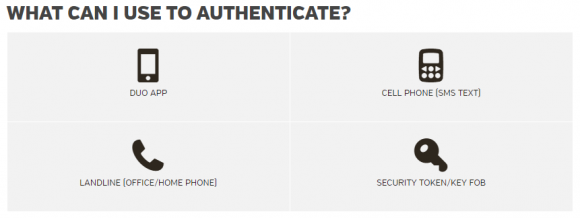
For now, BGSU is working on automating the opt-in for 2FA on university email. The 2FA system in front of its portal provides several 2FA options for students, including the Duo app, security tokens, or one-time codes sent via phone or SMS.
“If the numbers of compromised accounts keep increasing at the rate they are, we may get to that next level a lot sooner than our current roadmap for email access,” Haschak said.
2FA, also called multi-factor authentication or two-step verification, is a great way to dramatically improve the security of on online account — whether it’s at your bank, a file-sharing service, or your email. The idea is that even if thieves manage to snag your username and password — through phishing or via password-stealing malware — they still need access to that second factor to successfully impersonate you to the system.
Are you taking full advantage of 2FA options available to your various online accounts? Check out twofactorauth.org to find out where you might be able to harden your online account security.
Source: Krebsonsecurity


